Tired of being HACKED? HELP us HELP you!!!
Secure your important email & financial accounts with the convenience of using a single password…
Help kick HACKERS to the CURB!

We are Invysta Technology Group. Our goal in this campaign is to raise funding to introduce and launch ourUniversalSignin.Com(USi) data security service, targeted at consumers around the world. We are the developers of the Patent-Pending Active Security Key technology, giving you complete control of those Smartphones, computers and tablets that have authorization to access your important digital accounts. We areintegrating our technology into a service to protect you, the consumer, from the damage that can be caused when your digital identity is compromised.
So what’s the problem???
How does this affect you – the consumer?

Most consumer-oriented digital services operate in a user ID/password environment. Think about your email, social media, cloud storage and e-Commerce accounts, as well as online banking transactions. Account providers attempt to implement various digital protection schemes to defeat breached credentials. But being digital in nature makes them subject to the same attacks that hackers have used to penetrate large websites and collect a profile of digital information about you. Once that personal information has been harvested, you are fair game for the hackers.
Have you ever experienced the following?
- The contents of your email becoming known to unauthorized viewer … think Sony
- Have you ever had social media or Twitter messages attributed to you … but hey, you didn’t send them
- Ever had someone get into your cloud storage accounts? It happens, and even celebrities have had their most personal photos and videos spread around the web for all to view
- Who hasn’t had the experience where we go to use our ATM or credit card and guess what … no funds available. This has become even more of a problem, given the rise in online purchasing and the porous nature of existing digital security
- Some social media accounts have the potential to create a great deal of embarrassment and consequences … think Ashley Madison
Why did we start www.universalsignin.com?

It started with a Good Idea! We began the process of linking physical devices to authorization of account access in 2010. Our initial effort revolved around encryption technology. That interest has morphed into our current focus on providing a non-digital element in the account authorization process. Our goal has been to move the hacker community out of its digital comfort zone, and to remove scale from the damage they can do with breached user credentials.
How doesUSikeep your important accounts safe?

WithUSi we focus on the obvious. That means eliminating the hackers’ ability to access your accounts by simply entering user IDs and passwords gained in massive data breaches occurring weekly. Our goal is to securely lock-up the “front door” to your accounts! We have accomplished this by developing ourActive Security Keytechnology, which integrates the unique identity of your hardware devices into the accountauthorizationprocess. It is likely a given that if you have ahealthy online lifestyle, your credentials have become part of a hacker database. A hacker can use your breached credentials to access your accounts by simply going to a different computing device and using these credentials to access your accounts.
Some account providers presentdigitalhoops to jump through if the account suspects it is being accessed in an unauthorized manner. However, the key word here isdigital. If the hacking community is good enough to get the data in the first place, putting a fewdigitalobstacles in the way of experienced hackers, provides little in the way of real security. With USi, we introduce the identity of the physical device making the access request into the account authorization process, thus taking hackers out of their digital comfort zone.
USi is also a password manager on Steroids …

How our Active Security Key Protects you!

Have you ever heard the phrase, “they catch the ants while the elephants walk by?” There are many companies involved in trying to improve digital security. However, it has become apparent that many of these elaborate defense schemes ignore the obvious and focus on the corner cases.
Our Patent-Pending Technology!

We have worked hard to develop our technology and believe we have created something special and unique. The founders of Invysta have filed a number of patent applications covering our basic Active Security Key technology used in your USi account. The founders of the company are experienced in the pursuit of patents, and are listed inventors on nearly 40 issued utility patents.
What devices can you register to your USi account?

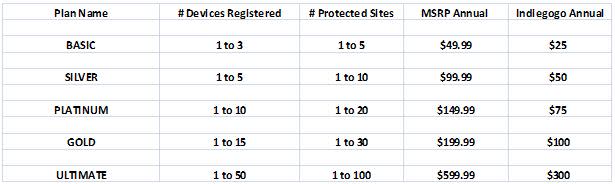
What protection plans does USi offer?

USi offers a number of plans for consumers, as well as our Ultimate plan for small business. We also can work directly with larger businesses or government to meet their needs. These plans are based on the number of devices you wish to register for access to your strategic accounts, and how many accounts you wish to protect.
How do I setup and usemy USi account?
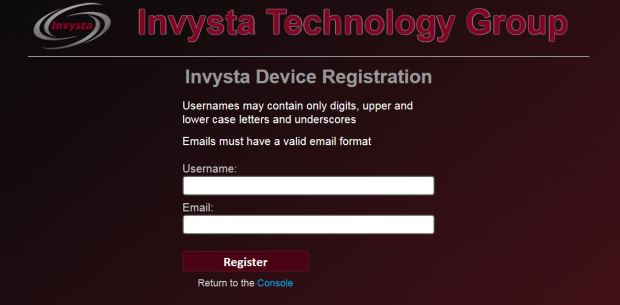
Registering a device to your USi account :
- During the account creation process, you will be asked to select a single password that will control access to the USi site, and all of your protected accounts.
- Once your USiaccount has been established, your first device can be registered to the account.
- USi pushes a client agent to the device being registered that agent has a unique number which identifies the account with USi.
- Once the client agent is installed, USi sends a character key that collects a set of predefined hardware and software identifiers, as specified by the character key.
- Once these identifiers are collected, they are submitted to the USi cloud manager which controls the USiValidation Database.
- The USi account holders can repeat the process and register as many devices as specified within the USiplan they purchased.
Adding a Website to your USi account:
- Once the first device has been registered to yourUSiaccount, you may begin adding strategic website accounts from the list of USisupported sites.
- You may add sites up to the number defined within the plan you purchased.
- During this process you will be asked to provide the current user name and current password required to access your account on the selected site.
- USi creates a random password of hashed data corresponding to the password template which matches the selected site.
- USielectronically accesses your selected account, and executes a change password routine, inserting the new hashed password created by USi.
- Some websites may require independent validation of the password change from the account holder.
- Once the password change procedure is complete, that account can only be accessed by a device that is already registered in the USi validation database.
- You no longer need to fear that your selected sites can be accessed, based solely on your username and password which may already have been breached.
Accessing a USi protected website or account:
- Go to www.universalsignin.comfrom a hardware device you have previosly added to your USi account.
- Enter your USi username and password.
- The USi system institutes a regeneration of the specified identifiers from the device initiating the access request.
- The regenerated identifiers are then matched against the identifiers that were stored in the USivalidation database at registration.
- If the regenerated identifiers do not match the identifiers stored in thedatabase, a match is not confirmed, and the account access request is denied.
- If a match of the identifiers to those stored in the database is confirmed, you are then presented with a listing of the websites/accounts that you have previously added to your USiaccount.
- You may now select the account that you wish to access, and USi automatically submits the username and the machine generated hashed password allowing you to access the account.
- Just one username and password to remember, while adding the security of knowing that your accounts can only be accessed from a hardware device you have registered, and not from any of the billions of other devices around the world!!!
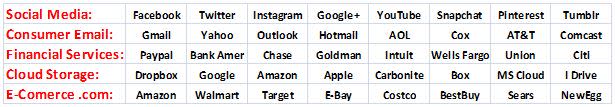
What type of accounts should I register with USi?

There is no need to register all the online accounts you access and use. Many of them are informational and do not represent a threat to you, even if they are hacked. We recommend adding strategic accounts to your USi protection plan … accounts which if breached, could cause financial consequences or damage to your good name and credit score.
- Personal Email Services
- Social Media/Dating Sites
- Financial Accounts (Banking/Credit Card)
- E-Commerce sites you use
- Your Cloud Storage
The following table reflects the initial target websites we anticipate supporting at product launch. We will continually be adding additional sites to our support list, based heavily on the input of our customer base.
10 Things To Know AboutUSi!

What will the funds be used for?

What is the purpose of the Metal Wallet perk?

For some years the Credit Card Industry has been moving toward a change in the method used to store card information and personal data on credit cards. The old magnetic stripe that has been a staple of identification information for many years, had simply outgrown its usefulness and is very vulnerable to being compromised. The new technology implemented was embedding an radio frequency ID tag (RFID)enabled chip into the card, as a replacement for the mag stripe.
Seemed like a good idea at first. However the hacking community was able to design devices, some for as little as $8, that allowed a hacker to access and record the information on the chipped card with a very simple scanning device. This can be accomplished by simply walking up to you, even when your credit cards are in your wallet or purse.
The aluminum wallet we are offering as part of our perk, shields the chipped card and defeats the scanning devices used by the hackers.
To understand more about why we have chosen to offer this simple solution as a perk, simply go to Google Search and type in“RFID hacks of chipped cards”… you will get about 246,000 results. A quick link to understand this problem is a three minute YouTube video athttps://www.youtube.com/watch?v=vmajlKJlT3U.
(Color may vary based on availability)
Risks & Challenges

As with any venture, risks and challenges are always a part of the landscape. We believe that our experience and dedication to what we are doing helps us to minimize those risks. Our Active Security Key technology is working in beta form on Windows platforms, and we are in the process of porting it to Android/Chrome platforms, following with Apple OSX and iOS devices and Blackberry.
Our initial market focus was to work with business and government to offer IT professionals the tools to keep unauthorized hackers from gaining access to their networks and accounts. However, the continued breaches involving consumers’ digital ID information has convinced us that we also must focus our attention on how we can help people regain control over their digital identity. The frustration and damage inflicted by these breaches has convinced us that we also need to launch our USi service to offer consumers real protection against the use of their breached data.
We understand the challenges we face and are dedicated to bringing digital data security to the people who so desperately need it.
When will the perks be fulfilled?

Perks will only be available to contributors from the United States. We expect to expand to foreign markets in early 2017, and may consider another campaign in those areas when we are ready to expand.
Pitch in and let’s make the digital world safer!!!

We realize that some people simply can’t afford to contribute to our campaign. But that doesn’t mean you can’t be part of the solution to this worldwide problem! Help us promote our campaign through word-of-mouth, and by asking people you know to use the Indiegogo share tools to make others aware of the good we can do in combating digital fraud.
Thanks in advance for your help and support.
Sincerely,
Team Invysta
We are Invysta Technology Group. Our goal in this campaign is to raise funding to introduce and launch our UniversalSignin.Com (USi) data security service, targeted at consumers around the world. We are the developers of the Patent-Pending Active Security Key technology, giving you complete control of those Smartphones, computers and tablets that have authorization to access your important digital accounts.
Youtube: https://youtu.be/apbshCfN0QQ
See Campaign: https://www.indiegogo.com/projects/tired-of-being-hacked-help-us-help-you
Contact Information:
Gary Streuter
Tags:
Indiegogo, Crowdfunding, English, News Category, United States, Reward-Donation, Global Regions, Language

The post Tired of being HACKED? Help kick HACKERS to the CURB! Secure your important email & financial accounts with the convenience of using a single password appeared first on iCrowdNewswire.
Source: Icrowdnewswire





